It is a rare occurrence but there were cases of call fraud where several misconfigurations led to the unnecessary exposure and compromisation of 3CX. We are going to highlight some common mistakes that lead to call fraud and what can be done to avoid them.
What is a Call Fraud?
Simply put, a call fraud occurs when untrusted parties place calls through your PBX, at your expense. Usually this happens overnight or when offices are closed, and calls are placed in bulk to various international destinations. And then you get a large bill at the end of the month which you need to pay….
Since the early ages of PBXs, free international calling has been the target of phone phreaks. You might think that it is something of the past with communication costs having drastically decreased. However, in the modern age of VoIP telephony, a global threat of organized crime has occurred to make big profits in an industrial manner.
Usually, a hacker compromises IP PBX servers in order to establish calls to premium international numbers. His motivation is an indirect financial gain. He will dial thousands of numbers in an automated manner from premium services under his control and paid with commissions per call or per time spent on the line. This is also known as the International Revenue Sharing Fraud (IRSF). There is another common way to profit more directly. It is the simple resale of stolen credentials on the darknet for whoever wants a cheap route to dial out.
3CX Phone System has many inbuilt security features and default settings. These features and settings prevent such abuses. However, administrators sometimes disable safeties without understanding the risks implied leading to the inevitable.
We will detail below the TOP 5 common mistakes to avoid.
Number 1: Weak Credentials that Increase the Chance of Call Fraud
The first mistake is using weak credentials for your extensions.
When creating an extension in your phone system, default random credentials are generated at all levels. Such as strong SIP Authentication ID and password for SIP, strong password for web client, for hard phone web interface, random voicemail PIN, etc. You should stick to those random values which ensure protection against password-guessing attacks, also called brute-force.
Since v15.5, it is impossible to edit and save an extension with credentials that are too short. However, you may have inherited such a setting from previous versions or backups.
There are warnings for admins when they have weak credentials by signaling a warning flag next to extensions names. If you hover over the extension you will get more information on the issue:
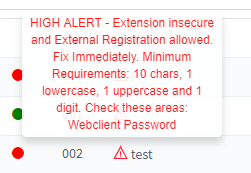
Please never set temporary credentials for testing if you will change them later when going in production. Usually people tend to forget these things.
Number 2: Allowing Remote Access
The second most common mistake is to untick the option “Disallow use outside LAN” under your extensions when not needed.
This option prevents remote SIP registration on your extension and is ticked by default when creating an extension. You can still use a remote 3CX client or the 3CX Web Client under this condition without being affected. Because the client uses the tunnel protocol to connect to the PBX. In effect, untick the option only when using a remote STUN hard phone.
Number 3: Too Many Countries Allowed
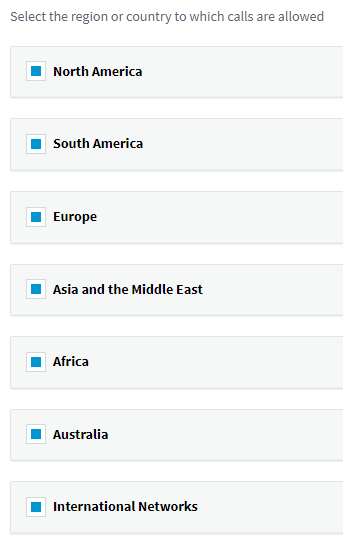
When first installing your PBX a screen prompted for the countries to allow in and outbound calls. This list can be found in the Security / Allowed country codes.
It should be restricted to the countries called commonly by the users. By default we restrict to the country of installation only.
A bad practice is of course to allow all countries thinking that it will be adjusted later, usually never.
Note for US customers: the North American Numbering Plan (NANP) allows to dial 25 regions or countries from North America and the Caribbean, without an international dial code The international dial code would be 011, or + in case of US. The anti-hacking feature will let such numbers go through as local numbers (as per ITU standards). You should therefore have strict outbound rules, with a list of NANP prefixes to block and route 1: Block calls, and ensure this rule is in first position.
The international dial code would be 011, or + in case of US. The anti-hacking feature will let such numbers go through as local numbers (as per ITU standards). Therefore, strict outbound rules are needed with a list of NANP prefixes to block and route 1: Block calls, and ensure this rule is in first position.
Number 4: Lazy Outbound Rules
Another bad practice is to have “lazy” outbound rules, letting any number dialed from anyone in the system go through. A typical rule is one with no criteria other than the DEFAULT extension group.
You should have rules set as strictly as possible. For instance in firewalls, define specific prefixes or number lengths, which extensions or extension groups are allowed to dial out.
Number 5: Misconfigured E164 Settings
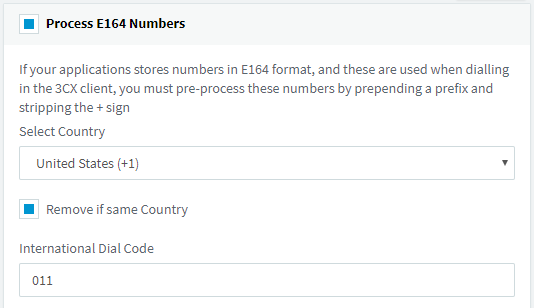
Under Settings / E164 Processing are standard settings ensuring the replacement of the “+” by your local international dial code. The reference is the country defined at the installation time. For example, in most countries you will get “00” as the international dial code; for the US you will get “011”. Those are values as per ITU standards.
This setting is important. As it is also used to determine the list of country codes blocked as per the “Allowed country codes” tab discussed above.
For instance, with “00” and Albania blocked, the feature will look for numbers dialed in the form of 00355xxx or +355xxx. If you misconfigured the international dial code, this can result in a wrong “+” replacement but also in the safety being inoperant.
Note that in most call fraud schemes observed, a cumulation of the previous 5 mistakes resulted in compromisation. One alone would usually not be enough for an attacker to be successful.
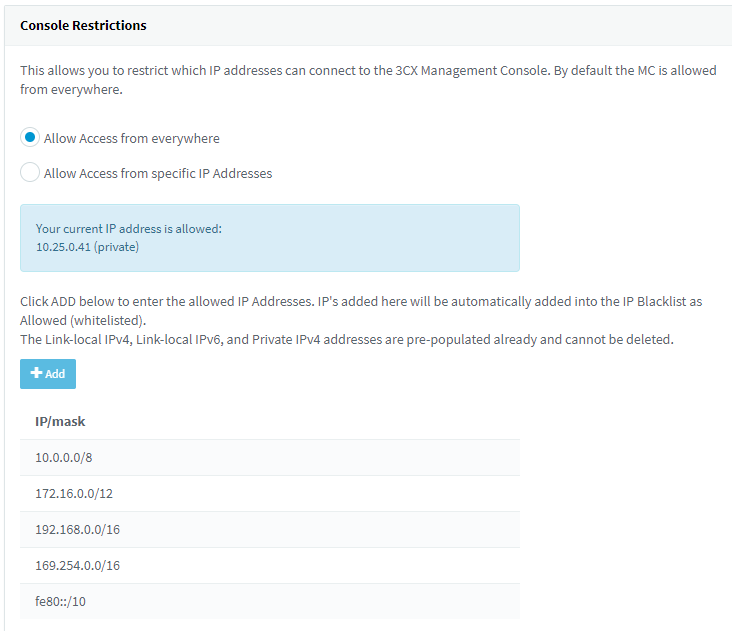
In v16 we introduced two major security features improving the security posture of 3CX even more. The first one allows you to restrict management console access based on the IP and is in Security / Security Settings / Console Restrictions. By default, all IPs are allowed. If enabled it will let through only local IP subnets and specified public IPs. This option does not interfere with other web services such as provisioning, web client, etc.
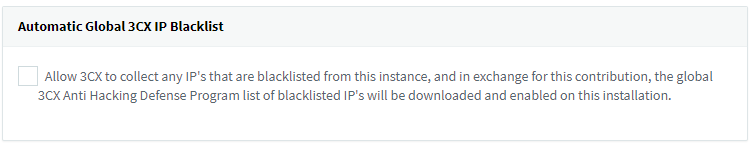
The second major improvement is the Automatic Global 3CX IP Blacklist, available in Security / Security Settings / Anti-Hacking. When this is enabled, your PBX will report any blacklist event including the attacker IP to the centralized server. After evaluation, recurring attackers are added and spread across all 3CX systems. This feature is enabled so that any malicious traffic will be dropped. To date this global blacklist has already got 1000+ common IPs and ranges which have been reported as scanning or frauding. We encourage you to enable this feature.
We look forward to receiving your comments on this topic!

